Android security flaw puts phones at risk
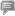 0 Comment(s)
0 Comment(s) Print
Print E-mail Shanghai Daily, September 30, 2012
E-mail Shanghai Daily, September 30, 2012
Cellphones using Google's Android operating system are at risk of being disabled or wiped clean of their data, including contacts, music and photos, because of a security flaw that was discovered several months ago but went unnoticed until now.
![Android security flaw puts phones at risk.[File photo] Android security flaw puts phones at risk.[File photo]](http://images.china.cn/attachement/jpg/site1007/20120930/001372acd0b511d1fd510b.jpg) |
|
Android security flaw puts phones at risk.[File photo] |
Opening a link to a website or a mobile application embedded with malicious code can trigger an attack capable of destroying the memory card in Android-equipped handsets made by Samsung, HTC, Motorola and Sony Ericsson, rendering the devices useless, computer security researcher Ravi Borgaonkar wrote in a blog post on Friday. Another code that can erase a user's data by performing a factory reset of the device appears to target only the newly released and top-selling Galaxy S III and other Samsung phones, he wrote.
Borgaonkar informed Google of the vulnerability in June, he said. A fix was issued quickly, he said, but it wasn't publicized, leaving smartphone owners largely unaware that the problem existed and how they could fix it.
Google declined to comment. Android debuted in 2008 and now dominates the smartphone market. Nearly 198 million smartphones using Android were sold in the first six months of 2012, according to the research firm IDC. About 243 million Android-equipped phones were sold in 2011, IDC said.
Versions of Android that are vulnerable include Gingerbread, Ice Cream Sandwich and Jelly Bean, according to Borgaonkar. He said the Honeycomb version of Android, designed for tablets, needs to be tested to determine if it is at risk as well.
Samsung, which makes most of the Android phones, said only early production models of the Galaxy S III were affected and a software update has been issued for that model.
The company said it is conducting an internal review to determine if other devices are affected and what, if any, action is needed.
Borgaonkar, a researcher at Germany's Technical University Berlin, said the bug works by taking advantage of functions in phones that allow them to dial a telephone number directly from a web browser. That convenience comes with risk, however. A hacker, or anyone with ill intent, can create a website or an app with codes that instruct the phones linking to those numbers to execute commands automatically, such as a full factory reset.